Understanding the Steps to Recovering a Secret with the DecRec Protocol
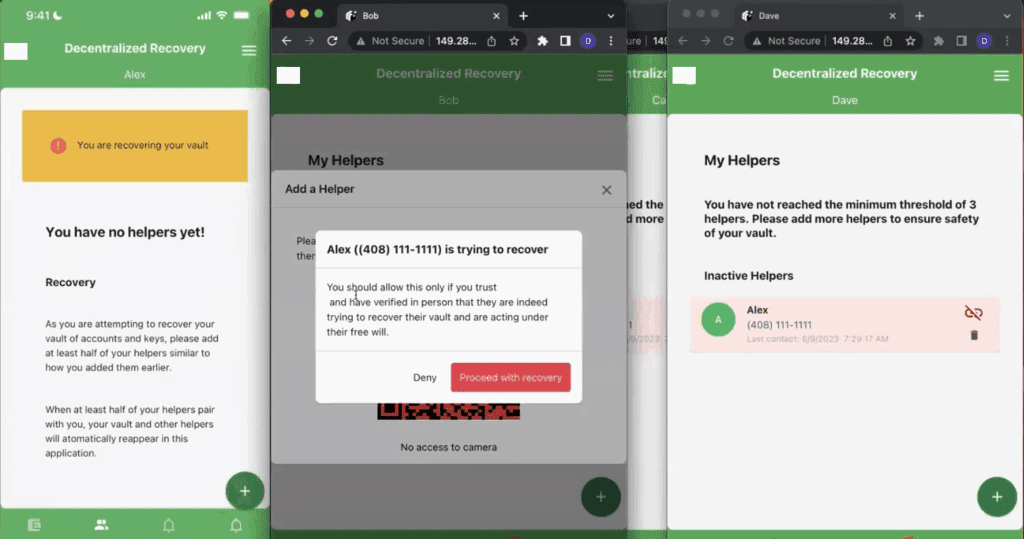
Once a secret has been protected with a DeRec Protocol-compliant application, see what it looks like for a user to recover that secret in this step-by-step demonstration of a typical DeRec user experience. This is part 2 of a 2-part series.
Understanding the Steps to Protecting a Secret with the DecRec Protocol
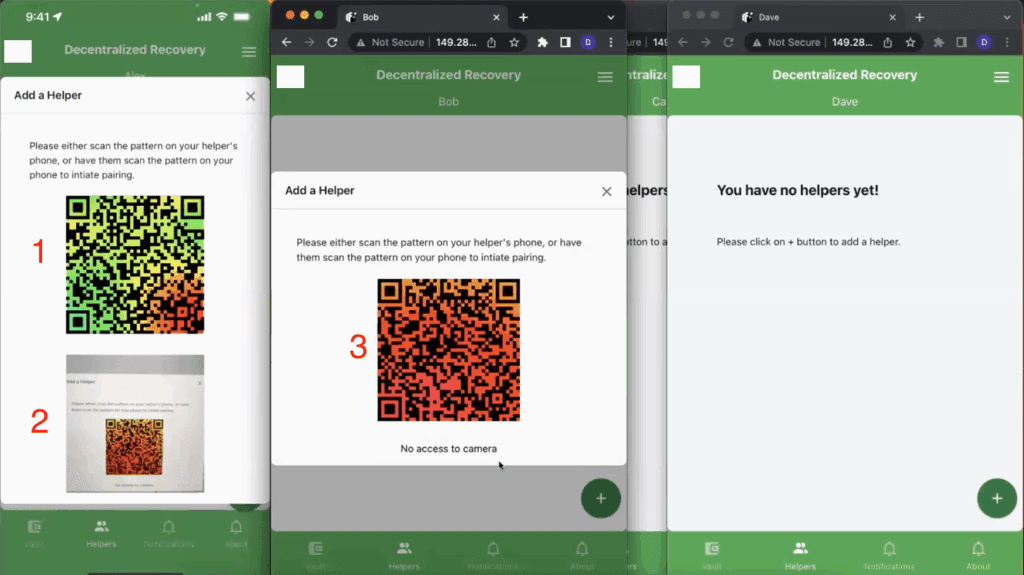
If you’re an end-user or developer, see what a typical workflow looks like when protecting a secret with a DeRec Protocol-compliant wallet, website, or other application. This is Part 1 of a 2-part series.